Tuesday, December 15, 2015
No, sir, I have no experience but I'm a big fan of money.
Friday, December 11, 2015
Interesting Phish
Wednesday, December 9, 2015
Cyber Chip - Scouting info
Today's youth are spending more time than ever using digital media for education, research, socializing, and fun. To help families and volunteers keep youth safe while online, the Boy Scouts of America introduces the Cyber Chip. In developing this exciting new tool, the BSA teamed up with content expert NetSmartz®, part of the National Center for Missing and Exploited Children® and training expert for many law enforcement agencies.
Netsmartz® has created a Scouting portal showcasing Cyber Chip resources, including grade-specific videos, for each level. Check it out here.
Topics include cyberbullying, cell phone use, texting, blogging, gaming, and identity theft.
http://www.scouting.org/Training/YouthProtection/CyberChip.aspxThursday, November 26, 2015
Thursday, November 12, 2015
Pentagon Farmed Out Its Coding to Russia
Friday, September 25, 2015
Rare and red supermoon lunar eclipse to present Sunday night spectacle - The Washington Post
With clear skies on the evening of Sept. 27, the plump Harvest Moon takes on crimson coloring – during a total lunar eclipse. Don your fall jackets, grab a hot mug of hot chocolate – with marshmallows, of course – and meet the neighbors outside for a cosmic chat. Watch heavenly glory unfold.
To make matters more interesting, the reddish, eclipsing moon will be in "perigee" phase – which means it is closest to the Earth for September, and in fact, it is the closest point all year – what some call a "supermoon." A so-called supermoon appears 14 percent bigger and 30 percent brighter than when the moon is farthest away from Earth.
https://www.washingtonpost.com/blogs/capital-weather-gang/wp/2015/09/24/rare-and-red-supermoon-lunar-eclipse-is-sunday-night-spectacle/Wednesday, September 23, 2015
SharpKeys | randyrants.com
http://www.randyrants.com/category/sharpkeys/
Wednesday, September 16, 2015
This is the same "group of veterans" that Trump praised and raised money for on the USS Iowa...
http://www.motherjones.com/politics/2012/05/swift-boat-obama-bin-laden-video
Monday, August 24, 2015
Elon Musk's Hyperloop - the futuristic transportation system that’s faster than an airplane to start construction in 2016
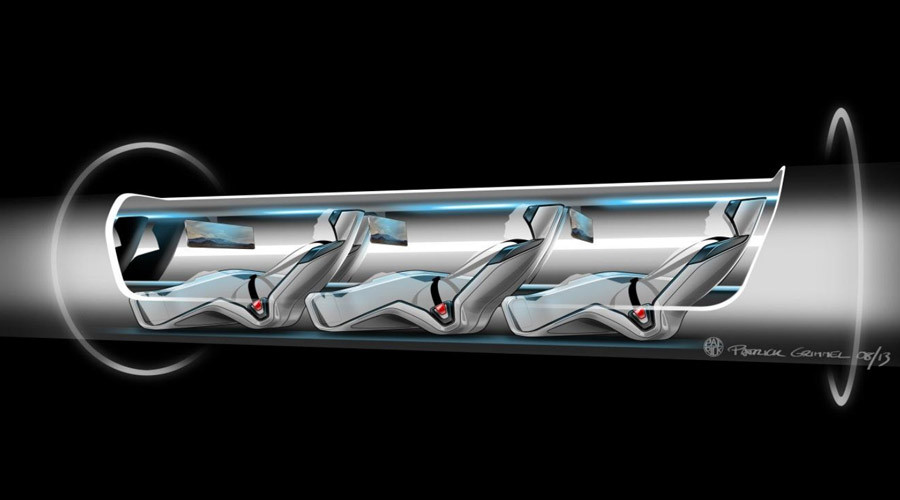
A public opening of the five-mile test track in Quay Valley, California is slated for 2018.
Tuesday, July 21, 2015
fsn - "It's a UNIX system! I know this!"
Why We’re Not Recommending “FIPS Mode” Anymore - Microsoft Security Guidance - Site Home - TechNet Blogs
More:
http://blogs.technet.com/b/secguide/archive/2014/04/07/why-we-re-not-recommending-fips-mode-anymore.aspx
Thursday, July 16, 2015
Monday, July 13, 2015
OPM hack includes 1.1 Million fingerprints too...
An entire biometric factor is now worthless.
http://money.cnn.com/2015/07/10/technology/opm-hack-fingerprints/index.html
Sunday, July 12, 2015
Monday, July 6, 2015
US jets intercepted Russian bombers off the California and Alaska coasts on July 4
The first incident reportedly occurred at 10:30 am ET off the coast of Alaska, when NORAD identified the Russian planes and two F-22s hurried to intercept them. Another incident occurred at 11 am ET off the coast of central California, and was responded to by two F-15s.
The Russian bombers they intercepted are capable of carrying nuclear weapons, but sources do not indicate whether or not they were armed.
More:Thursday, June 25, 2015
Sunday, June 14, 2015
Thursday, June 4, 2015
Sourceforge Hijacks the Nmap Sourceforge Account
From: Fyodor <fyodor () nmap org>
Date: Wed, 3 Jun 2015 00:56:23 -0700
Hi Folks! You may have already read the recent news about Sourceforge.net hijacking the GIMP project account to distribute adware/malware. Previously GIMP used this Sourceforge account to distribute their Windows installer, but they quit after Sourceforge started tricking users with fake download buttons which lead to malware rather than GIMP. Then Sourceforge took over GIMP's account and began distributing a trojan installer which tries to trick users into installing various malware and adware before actually installing GIMP.
More:http://seclists.org/nmap-dev/2015/q2/194Monday, May 25, 2015
Google: Security questions across websites are very easy to guess
For example using a single guess an attacker would have a 19.7% success rate at guessing English-speaking users' answers for the question "Favorite food?"
… With 10 guesses an attacker would be able to guess 39% of Korean-speaking users' answers to "City of birth?"
As for English-speakers favorite food, the most common answer is, not too surprisingly, "pizza."
More:
http://bgr.com/2015/05/22/google-security-passwords-secure-easy-guess/
Thursday, April 16, 2015
First time at RSA Conference? How to have the most fun. #RSAC
Wednesday, April 8, 2015
Google Mobile-Friendly Test
https://www.google.com/webmasters/tools/mobile-friendly/
Tuesday, February 24, 2015
VA Secretary Robert McDonald apologizes for misstating military record - The Washington Post
Wood quoted retired Army Col. Gary Bloomberg, a former Special Forces commander, calling McDonald's claim "a boneheaded statement." But Bloomberg said he and other former special ops officers did not consider it as egregious as some other misrepresentations.
"No one got really crazy about the whole thing, compared to some of what we've seen," he told the Huffington Post. "It's a lot different from guys running around faking their special forces credentials. … I can see [other former special forces soldiers] going, 'Hey, check out this boneheaded remark,' but I don't see the gravitas that I would with a guy wearing medals he didn't earn.'"
Monday, February 23, 2015
What Good is Tor in 2014?
It's probable, especially in the wake of the recent NSA revelations, that government agencies such as the NSA and CSIS sniff traffic on many exit nodes.
More:
http://resources.infosecinstitute.com/good-tor-2014/
Friday, February 20, 2015
Replacements - The Ledge Lyrics
Wow. Strong and sad. I think I knew that kid.
I'm glad I was able to get tickets today.
See you guys in DC in May.
http://www.metrolyrics.com/the-ledge-lyrics-replacements.html
Thursday, February 12, 2015
Jeb Bush just revealed the social security numbers of a bunch of former constituents
In a ham-handed effort at transparency, the likely 2016 Republican presidential candidate Jeb Bush just released a trove of emailsfrom his time as Florida's governor—but the emails included confidential messages, personal information and even social security numbers from thousands of people. What was he thinking?
The un-redacted email dump was first identified by the Verge, which found emails that, among other things, discussed the firings of public employees. In some emails, petitioners sent their social security numbers to Bush, who was famously responsive to email inquiries from his constituents.
Friday, January 30, 2015
I was quoted in an FCW article on mobile device security.
Striking a balance with mobile device security
Agencies face a delicate balancing act when it comes to providing mobile security.
On the one hand, IT departments seek to extend endpoint security to a growing population of mobile devices. It's easy to see why: Smartphones can go missing along with agency data, and mobile devices in general can introduce malware to enterprise networks. On the other hand, employees want the ease of use of consumer technology, and agency managers covet the potential productivity boost.
More:
http://fcw.com/articles/2014/12/08/striking-a-balance-with-mobile-device-security.aspx
Thursday, January 29, 2015
Saturday, January 24, 2015
Best Alternatives to Tor: 12 Programs to Use Since NSA, Hackers Compromised Tor Project
More:
http://www.idigitaltimes.com/best-alternatives-tor-12-programs-use-nsa-hackers-compromised-tor-project-376976
Thursday, January 15, 2015
New CISSP Domains
CISSP Domains, Effective April 15, 2015
- Security and Risk Management (Security, Risk, Compliance, Law, Regulations, Business Continuity)
- Asset Security (Protecting Security of Assets)
- Security Engineering (Engineering and Management of Security)
- Communications and Network Security (Designing and Protecting Network Security)
- Identity and Access Management (Controlling Access and Managing Identity)
- Security Assessment and Testing (Designing, Performing, and Analyzing Security Testing)
- Security Operations (Foundational Concepts, Investigations, Incident Management, Disaster Recovery)
- Software Development Security (Understanding, Applying, and Enforcing Software Security)


